If Restore repeatedly shows “Preparing file list” and a recurring progress bar but gets no further then:-
Quit iDrive.
Stop all related processes.
Run services.msc
Find iDrive service.
Depending on what is offered, either Restart or Start
Restart iDrive and try again.
You might get a suspicious email from a friend and assumes that said friend’s computer or email account has been hacked. Conversely, a friend may tell you of a dodgy email they received from you.
Often neither of you has been hacked so what has happened?
A scammer somehow gets hold of an email with several recipients including yourself and your friend.
The scammer then picks an email address and sends a fraudulent email to you which seems to come from your friend. This is not difficult to do.
Often scammers might use an address similar to your friend’s one. So if friend’s email is gordonbennet47@hotmail.com they might create a fake email account called gordonbennet47@gmail.com or gordonnbennet47@hotmail.com and send you a mail from there. It’s easy not to notice the disparity.
Countermeasures
There’s not much than can be done, but as a precaution, get your friend or whoever the emails are seemingly coming from to change their email password. This is just in case they’ve suffered a phishing attack per below.
Phishing
A scammer needs to get into just one email account to start his devious strategy.
Usually this is done by sending out loads of convincing looking emails which encourage the recipient (the ‘patsy’) to open a link.
The patsy clicks the innocuous looking like is presented with a challenge like “As a security measure, please proceed by entering your email password”. Patsy enters this and is taken to somewhere unremarkable such as Amazon. The patsy shrugs and forgets the whole thing.
Meantime the scammer then has the password and access to their email. This is known as phishing.
The scammer scans the email account and finds a group email to, say, a dozen emails. Scammer can then start sending fake emails from one to the other in the hope that somebody falls for the scam.
Website hacking
People often use the same password for their email and everything else. Somebody doing this might register their details (email address and password) on a legitimate but badly secured website.
A hacker then cracks the site and gets the list of emails and passwords. There’s a good chance that in many cases the password used is the same as the email password.
As a countermeasure never register an account on a site using your email password, think up something else.
Dodgy data brokers
There are people on the so called ‘dark web’ who will buy email addresses from scammers and sell them on to other scammers. There’s a fair chance that your email address is lurking on a few dodgy databases along with those of some of your contacts and friends. There’s nothing you can do about this.
This process is only needed if your extender (‘Fred’) comes disconnected from the printer.
FRED
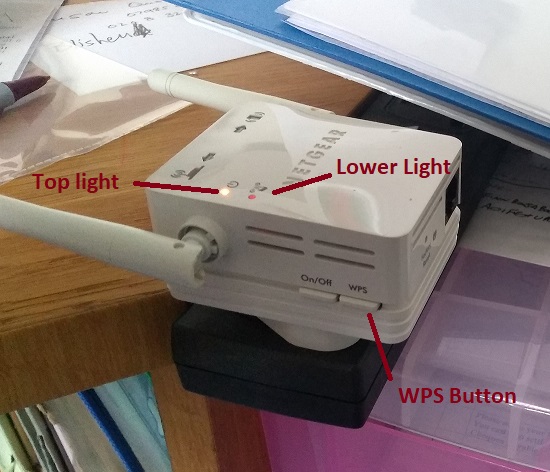
Plug Fred into a power source near to the printer and wait for top light to turn green.
PRINTER
Go to
SETTINGS
then
WIFI
then
WPS/AOSS
FRED
Press and hold the WPS Button until Lower Light starts flashing
PRINTER
Press OK
FRED
Relocate Fred to a suitable location, e.g. on landing as discussed.
Fred will survive being plugged in and unplugged.
When connecting to a website you might see the message “Your connection is insecure” or “your connection is not private” or “SSL certificate expired” accompanied by a not very helpful panicky message.
What causes this?
There are security safeguards to prevent you from being diverted to a fake website (see Compromised Computer below) which might trick you into giving up password or other information. They also encrypt data so that an eavesdropper on your network cannot read sensitive data. In practice this latter situation, though, is very unlikely.
So, what are the main causes and remedies of “insecure” messages.
Wrong date and time
If the date and time on your computer are not roughly accurate then this can cause the error, something which is easy to check. Older computers are more prone to this.
Slow internet connection
This can produce symptoms of an Insecure error.
Temporary website fault
Sometimes there is a configuration error on the website which you trying to access.
Maintenance problem on website
Secure access is validated by something called an SSL Certificate on the website. You don’t need to know the Science Bit but the certificate needs to be renewed from time to time. Sometimes this is overlooked by the website owner.
Compromised Computer
This is the least likely but it works as follows.
A trojan or virus created by a hacker finds its way into your computer.
It then interferes with the network settings such that when you go to certain websites it actually diverts you to a fake one.
On the fake site, you haplessly enter your username and password. This information is captured and the hacker can then log into the real website.
WHAT TO DO
Check the date and time on your computer.
Try accessing the website again after a few minutes. This won’t harm anything. If the problem persists then leave it for an hour or so before trying again.
Still problems? See if you can try the website from another computer. If it works fine then try again one last time from your own computer. If you still get the error then consult A222 and we’ll take a look.
Insert your backup disk. If Window pops up a ‘…what to do…’ then dismiss it.
Invoke Syncovery from the desktop or start menu. This is identified by the following icon.

If at top left there is a link saying “Switch to Advanced Mode” then please click.
RUNNING THE BACKUP
You’ll now be in the Profile Overview Tab.
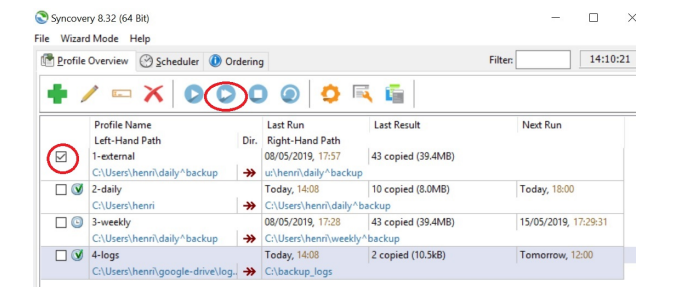
There are 4 profiles listed in this example:-
1-external
2-daily
3-weekly
4-logs
Your computer will have a different profile list.
Tick the box against 1-external or whichever you’ve received instructions for.
Press the Double Arrow in the toolbar at the top. Make sure you hit the double, not the single.

The backup will now run.
If an error is reported or if ANY of the profiles are highlighted in red then please note it and contact A222.
On completion, close the Syncovery program; disconnect the external disk; store it away from the computer.
CHECKING BACKUP
If on start up your get an ‘overdue’ message and there’s no good reason for anything to be overdue then consult A222.
Also, if any errors are indicated (highlighted in red) before or after you run the backup then consult A222 for advice.
OUTLOOK and BACKUP
If you use the Outlook desktop program then please don’t launch this at computer start up, wait for 5 minutes. This is to allow any email backup to take place.
In 2015 Windows 10 appeared and users of Windows 7 and 8 were offered free automatic updates.
Sometimes this went smoothly. At other times there were all sorts of problems: wifi no longer working, printer connections lost, programs no longer working.
Also in some cases when the update was successful, some computers almost ground to a halt because, whilst powerful enough to run Windows they could not cope with Windows 10 which was much more demanding of resource.
At the moment updates from 10 to Windows 11 are being offered. Anecdotal evidence suggests that there are no problems save for users needing to get familiar with a new system.
Things could, however, go wrong so please heed the following recommendations:-
Backup all data before allowing the update.
Ensure that you have access to the installation files for the programs which you use (in case they need to be re-instated).
Do the update at a quiet time so that any problems can be addressed before the computer is needed again.
A222 can, of course, help with all this.
We talk about ‘booting’ and ‘rebooting’ but where does the term come from.
Early computers started up by reading a short length of magnetic tape.
This was called, in geek-speak, the Bootstrap.
You have people receiving odd emails from you and assume you’ve been hacked. What has happened?
This is unlikely and one of the situations below is more likely. If you have other symptoms or are worried then I am happy to check your system, please get in touch.
Email hacking is not as easy as one might think, more likely you’ve been ‘phished’ – tricked into logging in to a fake site and your details have been compromised. Change your password and all should be well.
Depending on your email setup, it may not be difficult for a spammer to send out email as if it is from you. This usually happens when a group email including yours has fallen into the wrong hands – and this may be nothing to do with you directly at all.
This can be hard to tell from Phished per above. Change your password anyway.
Best practice is to use different passwords for different sites – at the very least have a unique one for your email.
If somebody has acquired your email address and password then they may try to log into other sites of which you have membership.
So, if you use other websites with the same email address and password as your email one then log in soonest and change the passwords on those sites.
I am no longer providing monitored antivirus and security systems.
Instead I am offering to install one of two very good products (Bitdefender or ESET) for which I will ask you to purchase the licence directly from the provider.
I will, of course, be happy to talk you through this process and provide whatever assistance is needed.
Installation is free for any computer on which I have installed Bitdefender or ESET in the past otherwise a small fee will be charged.
Prices are below to help you to calculate the best option. Bitdefender have frequent promotions so prices do vary.
| Bitdefender Total Security | 1 year | 2 year | 3 year |
| up to 5 computers | 42 | 120 | 150 |
| ESET Internet Security | |||
| 1 computer | 40 | 60 | 85 |
| 2 computers | 45 | 68 | 95 |
| 3 computers | 50 | 75 | 105 |